The Era of the Never-Ending Cyber Attack: The Closed Loop Process and DPaaS


Cyber attacks are not going away. In fact, the increased frequency in the past couple of years is startling. There were 2,365 breaches in the U.S. in 2023 with 343.3M victims. This represented a 72% increase since 2021, which held the previous all-time record. And the numbers are only expected to grow.
Organizations are rightly concerned about their own preparedness and ability to stay operational in the face of these threats. In our own most recent Modern Data Infrastructure Dynamics report, 69% of IT leaders surveyed were concerned their organization couldn’t detect a breach in time to protect their data. And 22% admitted their critical data wasn’t backed up.
As we are now in a “when,” rather than an “if” era, most organizations should have a clear understanding by now of their data storage vulnerabilities. As well as how best to prioritize protection and recovery elements. Assessments should not only focus on defense but also on how response plans can best support workflow prioritization and continuation of business-critical operations.
Adding complexity, many organizations now leverage hybrid cloud data storage environments. These can be particularly vulnerable, especially if necessary due diligence hasn’t been completed to determine potential gaps in coverage.
With the number of attacks growing at such an astonishing rate, organizations need to be planning for a continued “closed loop” response. One that feeds critical learnings back into their protection and readiness strategies to proactively guard against whatever comes next.
A closed loop process – one starting with a comprehensive audit and assessment to not only determine gaps in coverage, but that also informs a thoughtful strategy to prioritize the safety of mission-critical data – can keep organizations operational during and after an attack. As well as prepare them for next time.
The assessment aspect of the process is important for organizations needing to balance performance, risk, availability and cost. It can determine what data is important for mission critical workflows and what data is not.
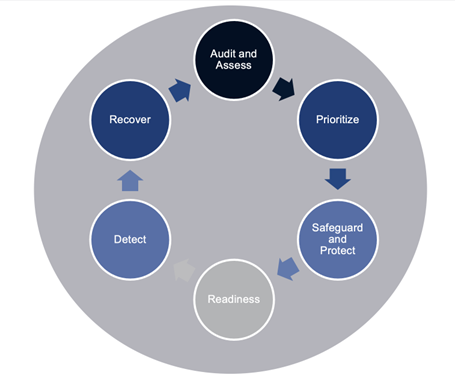
Also, to address the continued, never-ending attack mode that cybercriminals now employ, organizations need to have their readiness, detection and response/recovery plans firmly established and clearly communicated across the entire organization.
Just as importantly, learnings need to be fed back directly into the loop so the organization will be even more prepared next time.
Data protection as a service can help organizations quickly and easily augment their data protection strategy. As well as provide for greater resiliency by meeting an organization’s needs wherever they are in their closed loop planning journey. From assessment to planning to response.
Data Protection as a Service from Hitachi Vantara (DPaaS), part of the EverFlex portfolio of IaaS solutions, offers needed flexibility and choice for organizations to tailor solutions to their unique and evolving needs, as much or as little as required. Organizations can choose from bands of OpEx, subscription-based storage and compute components in ways that support protection and resilience strategy prioritizations. All while eliminating the risk of financial and technical over-commitment.
Plus, the ability to select from a full spectrum of consulting, management and support services enables organizations to get just the level of help they need to close their own protection and resiliency loop. Whether that be at the assessment or recovery stage, or anywhere in between.
DPaaS delivers in key ways to help any organization, wherever they are on their own individual closed loop journey. And providing them the ability to either do it yourself or fill skills and resource gaps with fully managed options. DPaaS services can even step in to help organizations with audits and assessments, as well as help develop strategies that factor in their current risk exposure, budget and business goals.
Once a strategy is in place, an organization can move to deploy quickly. Using DPaaS’ pretested or uniquely tailored designs, organizations don’t have to spend time and money building and managing their own data protection and cyber resiliency solution. Once deployed, DPaaS is ready to start working to meet any needed service level agreements (SLAs), recovery time objective (RTO) and recovery point objective (RPO) to address business goals, risk exposures and regulatory requirements.
Whether an organization is looking for a straightforward self-serve way to augment existing protection and resiliency strategy, or an organization has more complex needs and requires a trusted partner with a consultative approach, Data Protection as a Service from Hitachi Vantara provides an ideal path forward. In an era of never-ending cyber attacks, organizations need an equivalent, never ending closed loop response.

Kristan Ruona, Senior Product Marketing Manager for Data Protection as a Service from Hitachi Vantara (DPaaS) an Everflex IaaS portfolio offering.